PAUSED - (M)PSD: Pentester's Parcours
Project System Development
In the project system development, students work on a given computer science topic in a team under practical conditions. In terms of content, the project group works independently on current issues of practical relevance. The lecturer takes on the role of the client/customer. At the same time, however, he supports the team to set the right course, especially in the initial phase, and to get the project rolling.
In an introductory event, the task is first outlined and the framework conditions explained. During the project, weekly project meetings are held in which the results of the previous week are presented and the objectives of the coming week(s) are defined.
Topic
The aim of the project is to further develop an existing training infrastructure for pentesting. The purpose of this infrastructure is to provide a training environment for offensive security tests, i.e. it is the target of white-hacking attacks.
The environment simulates a company network consisting of several computers running different applications. Vulnerabilities were/are deliberately built in to allow attackers to gradually penetrate the system.
An important feature of the environment is that it can be easily restored to its original state. Another important feature is that the environment can be replicated without great effort. Both can be achieved using virtualization technologies. Last but not least, simple management of the infrastructure should be maintained through extensive automation.
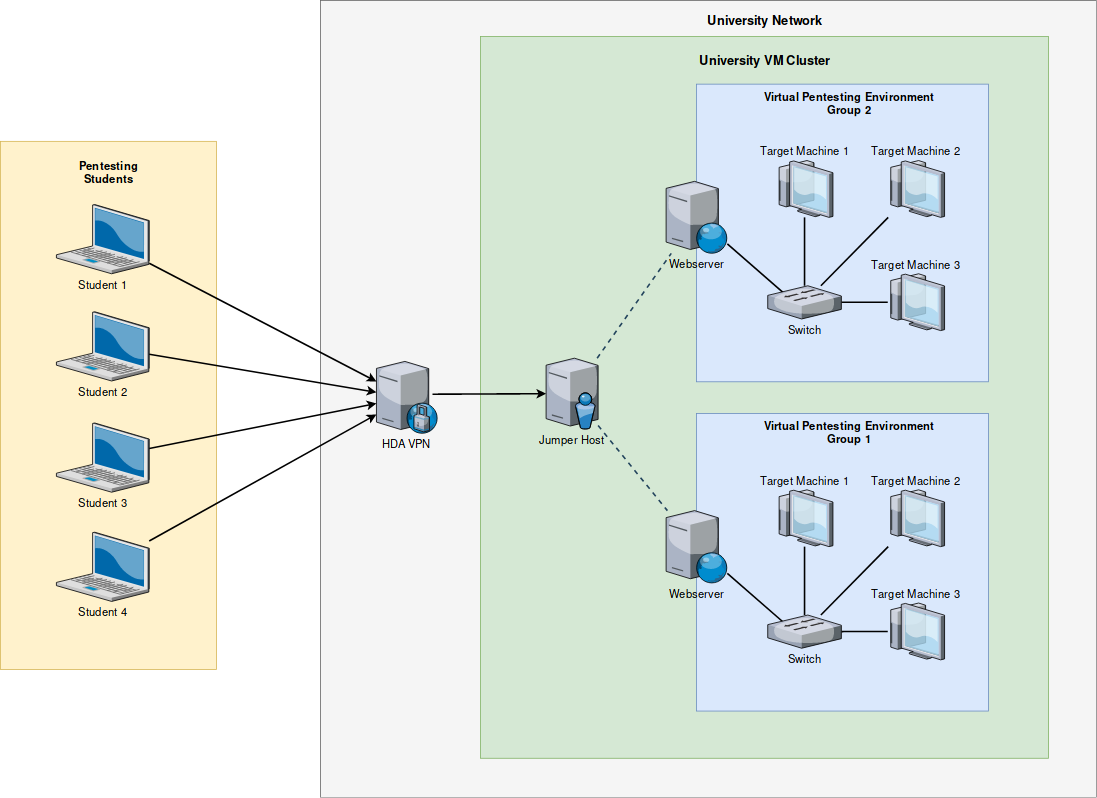
For example, this infrastructure could be used in relevant courses at h_da. Fig. 1 shows what such a training infrastructure for courses could look like. On the left-hand side of the figure you can see student computers that are connected to the university network via VPN. (Alternatively, the computers could also be connected directly to the university network via the university WLAN). Since not all students should work on the same test environment, they are distributed in groups by a jump host (center of the picture) to identical copies of the simulated company network (right in the picture). Each group then works exclusively on the environment assigned to it and has no access to the other environments. A single environment then consists of different (virtual) computers / applications. The only initial access point and the first attack target is a web server that can be reached from outside. Behind this, there are further targets that are to be attacked.
Scrum is to be used as the process model for agile system development. The usual development tools are used, preferably those that are already available in the department, e.g. GIT repository, Scrum board, etc.
The concrete scope and the expansion stage of the project depend, among other things, on the team size (number of participants) and the technical possibilities. It is planned to continue the project in future events. The project is under MIT license.
Contact
Communication
Schöfferstraße 10
64295 Darmstadt
Office: D19, 2.09
+49.6151.533-60185
alexander.wiesmaier@h-da.de
1
Consultation
Nach Vereinbarung / by appointment